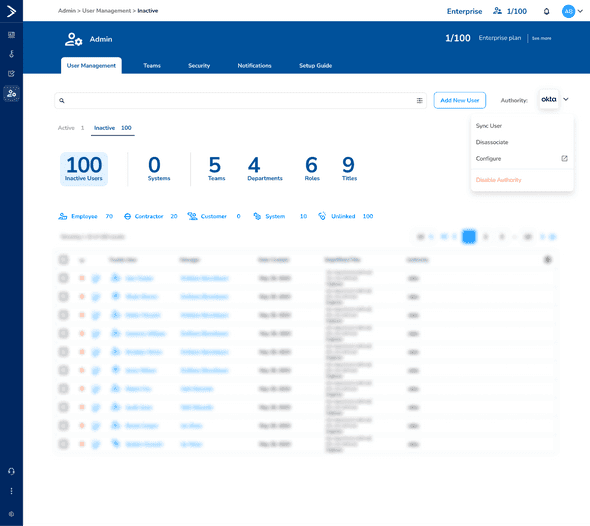
The Vandelay Chronicles: Simplifying User Management with Trustle’s Authority Feature
In our previous installments, we explored the challenges faced by Alice, Cal, and Jack at Vandelay Industries, and how Trustle's innovative solutions helped them streamline their access management and operational workflows. Today, we explore a new feature introduced to make access management even easier – the Authority feature. This much requested feature addresses a major pain point of being able to both source, and keep Trustle users in sync with enterprise IDPs, in addition to managing Trustle users not contained within IDPs (contractors, customers, systems, etc.)
The Challenge: Managing Users across disparate Identity Providers
Cal, the IT Manager, faces a recurring nightmare: managing user access and ensuring that the right people have the right permissions at the right time. The challenge is multifaceted:
- Fragmented User Information: Vandelay’s identity provider (IDP) is packed with user data, but it’s often outdated or incomplete.
- Disparate User IDP: Some users, like contractors or partners, are not managed in the primary IDP, making it difficult to manage their access separate from those in the IDP.
- Inefficient Processes: Existing processes for updating user information between Trustle and all upstream sources of truth can be cumbersome and time-consuming.
Introducing Trustle’s Authority Feature
Trustle’s Authority feature is designed to tackle these issues, providing a unified process to manage user information and access. Here’s how it works:
Up-to-date User Information
One of the most significant advantages of Trustle’s Authority feature is its ability to unify user management across multiple systems. By integrating with your IDP, Trustle ensures that all user information is synchronized and up-to-date. No more fragmented data or manual updates – Trustle automates the process, giving Cal peace of mind.
All Users, Single Solution
For users not present in the IDP, Trustle offers a simple yet powerful solution. The Authority feature allows Cal to onboard external users, such as contractors or partners, directly into Trustle. These users can be assigned specific roles and permissions, just like regular employees, ensuring they have the access they need without compromising security.
Streamlined Processes
It’s tough keeping user data up-to-date, but Trustle’s Authority feature simplifies it. With an intuitive interface and automated workflows, Cal can easily manage access in a single access management system, regardless of each users’ source of truth.
A Day in the Life of Cal, IT Director
Let’s take a closer look at how Trustle’s Authority feature transforms Cal’s daily operations:
Morning Routine: Syncing User Data
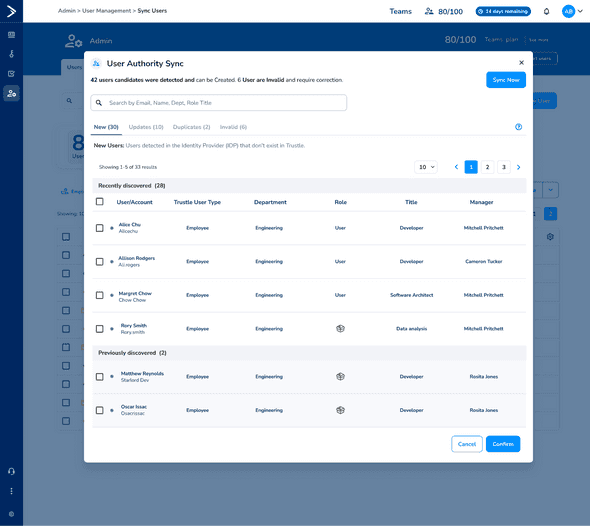
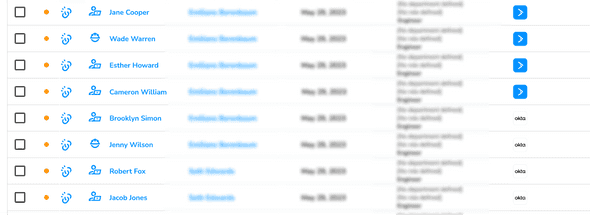
With the new User Authority feature, all user information from Vandelay’s sources of truth are automatically updated and synced with Trustle’s user directory, ensuring that Trustle has the most up-to-date user data. This automated sync process eliminates the need for manual updates and helps keep user data current. Gone are the days of Cal manually syncing user data!
Mid-Morning: Onboarding a New Contractor
Cal needs to onboard a new contractor, Emma, who will be working on a critical project. In the past, this would have been a lengthy process, involving multiple systems and manual approvals. But with Trustle’s Authority feature, Emma is already sync’d to Trustle. Cal merely approves her for the appropriate permissions, enabling Emma to start work in minutes versus days.
Afternoon: Updating User Information
Cal receives an email from HR notifying him of several changes in employee roles and departments. Using Trustle’s Authority feature, the changes are already in Trustle! With a few clicks, he can view and verify all updates sync’d from upstream, ensuring that everyone has the correct access based on their new roles. This automated process saves Cal hours of work and reduces the risk of errors.
Evening: Reviewing Access Logs
At the end of the day, Cal reviews the access logs and audit trails in Trustle. The Authority feature provides detailed reports on user access, including who has access to what resources, when access was granted, and by whom. This visibility is crucial for maintaining security and compliance, and it gives Cal the confidence that Vandelay’s access control is properly managed.
Before Trustle
- Fragmented Data: User information was scattered across multiple systems, leading to inconsistencies and outdated data.
- Manual Processes: Onboarding external users and updating information were manual, time-consuming tasks prone to errors.
- Security Risks: Lack of visibility into user access and outdated information increased the risk of unauthorized access and security breaches.
After Trustle
- Unified Data: All user information is synchronized and up-to-date, ensuring consistency across the organization.
- Automated Processes: Onboarding external users and updating information are streamlined and automated, saving time and reducing errors.
- Enhanced Security: Detailed access logs and audit trails provide visibility and ensure compliance, reducing the risk of security breaches.
Conclusion
Trustle’s Authority feature is more than just a tool – it’s a game-changer for organizations struggling with managing user access sourced from multiple IDPs and sources of truth. By providing a unified, automated, and secure solution, Trustle empowers IT leaders like Cal to manage user access efficiently and effectively.
Key Benefits of Trustle’s Authority Feature
- Unified User Management: Synchronize user information across multiple systems, ensuring consistency and accuracy.
- Easy Onboarding of External Users: Quickly onboard contractors, partners, and other external users, granting them the access they need without compromising security.
- Automated Updates: Streamline the process of updating user information, reducing the risk of errors and saving time.
- Enhanced Security: Maintain detailed access logs and audit trails, ensuring compliance and reducing the risk of security breaches.
- Improved Efficiency: Automate manual processes, freeing up time for IT leaders to focus on strategic initiatives.
More About Trustle
Read more about this new feature and try Trustle today! Sign up for a demo in just minutes. And don’t leave without checking out our blog for ongoing thought leadership and expert insights on identity and access management, cybersecurity and data security topics.